Hackers Attempt “Dictionary Attacks” on WordPress Websites

A WordPress Security firm, Defiant, recently discovered that a network of 20,000 botnets, controlled by hackers, is attempting “Dictionary Attacks” on other WordPress websites.
The security firm detected over 5 million login attempts in the last month from already infected WordPress websites. The attacks involve a series of repeated logins where the bots try different combinations of username and passwords.
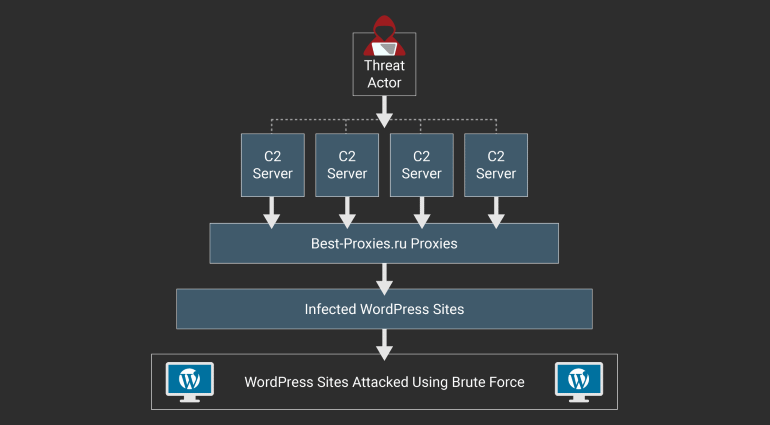
Mikey Veenstra, a Defiant security research analyst, states that they have figured out how this network of botnet operates. Apparently, on the top of this chain of botnets stands a command server that directs all the infected websites on which WordPress website to attack next.
Image credits: Defiant
The servers act as the dissemination of information and instructions to the infected website who then carry out the attacks. These servers relay the information to malicious scripts on already infected websites.
These scripts identify a list of target websites that are to be attacked and then generate passwords based on predefined patterns. The scripts then use the newly generated passwords to log into to other WordPress websites.
Veenstra has explained the script’s mechanism and how it works.
“If the brute force script was attempting to log on to example.com as the user alice, it will generate passwords like example, alice1, alice2018, and so on. While this tactic is unlikely to succeed on any one given site, it can be very effective when used at scale across a large number of targets.”
The attackers often use proxies to hide their identities, making it even more difficult to track and stop them. However, the capable team at Defiant identified loopholes in the execution of this attack which revealed the entire backend structure of this activity.
The research team at Defiant didn’t stop there. They stated that the attackers also made mistakes in implementing the authentication systems for their botnet’s admin panel. This allowed the researchers to have a peek inside the hacker’s operations.
Image credits: Defiant
Defiant has already reported the information with law enforcement agencies hoping that the attackers would be taken down. However, the botnet’s command control servers are hosted on HostSailor. HostSailor is known for being a bulletproof hosting provider that doesn’t take “takedown requests”. Which is why, sadly, the attacks are still ongoing and websites are being compromised.
How To Protect Your Website Against “Dictionary Attacks”?
The first thing that comes in your mind would be to change your website’s admin URL. This, however, won’t help in protecting your website because the attacks are directed at WordPress XML-RPC instead of the admin URL.
Defiant recommends using a WordPress security plugin to protect your website from such attacks that are carried out against XML – RPC service.
The good news is that since these attacks have been going on for a long time, any decent WordPress firewall service would be strong enough to stop them.

Create Faster WordPress Websites!
Free eBook on WordPress Performance right in your inbox.